VPC endpoint policy for CloudWatch Logs, CloudWatch Events
- First of all
- What's VPC endpoint?
- What's VPC endpoint policy?
- Use case of VPC endpoint policy
- Try
- Finally
First of all
I found that we could describe VPC endpoint policies for VPC endpoints of CloudWatch Logs and CloudWatch Events. I tried to verify the behavior.
I described about VPC endpoint and VPC endpoint policies, so skip if not necessary.
I am sorry for my poor English because I am not good at English.
What's VPC endpoint?
VPC endpoint is a endpoint to route a request to AWS API from VPC resources within AWS network.
Usually, if you want to send an AWS API request from an EC2 instance in a private subnet, you need to place a NAT Gateway (or NAT instance) in a public subnet, which means the request may be routed through the Internet. But VPC endpoints enable us to keep the request within AWS network.
What's VPC endpoint policy?
Speaking briefly, VPC endpoint policy is like a IAM policy. All requests through a VPC endpoint are constraint by the policy.
Even if you allow by IAM policy, a request is denied by a VPC endpoint policy with no allowance.
VPC endpoint has two types, "Gateway" and "Interface". Until now, we can describe VPC endpoint policy only for Gateway type(S3 and DynamoDB).
Thanks to this update, VPC endpoint policies of CloudWatch Logs and CloudWatch Events can now be described as Interface type VPC endpoints for the first time.
Use case of VPC endpoint policy
What are the benefits of using a VPC endpoint policy?
Firstly, I understand that you can restrict access to resources of other accounts.
Let's take S3 as an example.
When you use a VPC endpoint and a VPC endpoint policy with no restriction, it is possible to take data from EC2 to the S3 bucket of another account by using the access key of another account.
If confidential information etc. are stored on EC2, data leakage can occur in the following cases.
- System operation personnel operate with malicious intent
- OS command injection is performed for EC2
- EC2 infects with malware
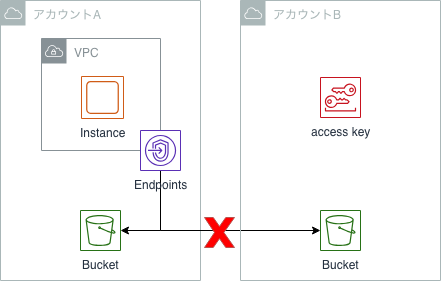
Therefore, when I use the VPC endpoint policy, I restrict a VPC endpoint policy only the resources of my account as correspondence to those risks.
Try
Preparation
- Create a VPC endpoint of
com.amazonaws.ap-northeast-1.logs Only if you chose com.amazonaws.ap-northeast-1.logs or com.amazonaws.ap-northeast-1.events, you can see a text box for a policy at the bottom.
Only if you chose com.amazonaws.ap-northeast-1.logs or com.amazonaws.ap-northeast-1.events, you can see a text box for a policy at the bottom. - Describe policy. I allowed only a request to a log group "log-group-allowed".
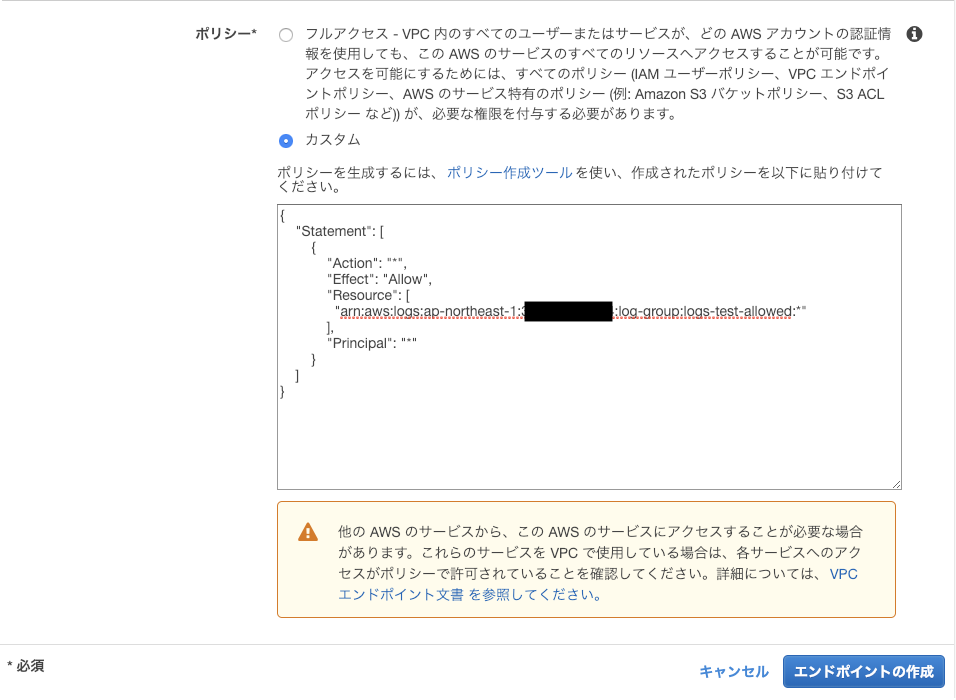
{
"Statement": [
{
"Action": "*",
"Effect": "Allow",
"Resource": [
"arn:aws:logs:ap-northeast-1:XXXXXXXXXXXX:log-group:logs-test-allowed:*"
],
"Principal": "*"
}
]
}
- Create an EC2 instance in a subnet you created the VPC endpoint.(I attatch to an IAM policy to an IAM role of the EC2 instance.)
- Create log groups and log streams.
$ aws logs create-log-group --log-group-name logs-test-allowed $ aws logs create-log-stream --log-group-name logs-test-allowed --log-stream-name logs-stream $ aws logs create-log-group --log-group-name logs-test-denied $ aws logs create-log-stream --log-group-name logs-test-denied --log-stream-name logs-stream
Verify a behaivor
Log in to the EC2 instance, then send a request.
Verify a route of requests
Using a dig command, I confirmed a request to logs.ap-northeast-1.amazonaws.com was routed to the VPC endpoint.
Private IPs were gotten, then I confirmed.
[ec2-user@ip-172-31-29-146 ~]$ dig logs.ap-northeast-1.amazonaws.com ; <<>> DiG 9.9.4-RedHat-9.9.4-61.amzn2.1.1 <<>> logs.ap-northeast-1.amazonaws.com ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 30198 ;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;logs.ap-northeast-1.amazonaws.com. IN A ;; ANSWER SECTION: logs.ap-northeast-1.amazonaws.com. 60 IN A 172.31.10.218 logs.ap-northeast-1.amazonaws.com. 60 IN A 172.31.20.109 logs.ap-northeast-1.amazonaws.com. 60 IN A 172.31.44.227 ;; Query time: 2 msec ;; SERVER: 172.31.0.2#53(172.31.0.2) ;; WHEN: 土 2月 16 05:50:36 UTC 2019 ;; MSG SIZE rcvd: 110
Verify a behavior of policy
I sent a test data to the log groups, logs-test-allowed, logs-test-denied.
The put-log-events request to logs-test-allowed was suceeded.
[ec2-user@ip-172-31-29-146 ~]$ aws logs put-log-events --log-group-name logs-test-allowed --log-stream-name log-stream --log-events timestamp=1550295898001,message=ExampleEvent1 timestamp=1550295898002,message=ExampleEvent2
{
"nextSequenceToken": "49592304407703484745949521076996311451170380XXXXXXXXXXXX"
}
The put-log-events request to logs-test-denied was failed.
[ec2-user@ip-172-31-29-146 ~]$ aws logs put-log-events --log-group-name logs-test-denied --log-stream-name log-stream --log-events timestamp=1550295898001,message=ExampleEvent1 timestamp=1550295898002,message=ExampleEvent2 An error occurred (AccessDeniedException) when calling the PutLogEvents operation: User: arn:aws:sts::XXXXXXXXXXXX:assumed-role/ec2-logs-fullaccess-role/i-XXXXXXXXXXXX is not authorized to perform: logs:PutLogEvents on resource: arn:aws:logs:ap-northeast-1:XXXXXXXXXXXX:log-group:logs-test-denied:log-stream:log-stream
These have confirmed that the VPC endpoint policy is applied to the VPC endpoint of CloudWatch Logs.